Carlos Trejo
martes, 5 de noviembre de 2013
Caso N8
http://www.youtube.com/v/1Q1YXtnFKq4?version=3&autohide=1&autohide=1&feature=share&showinfo=1&attribution_tag=4o0jYXxE0n1EKM-wPHUxFQ&autoplay=1
domingo, 28 de julio de 2013
domingo, 2 de junio de 2013
lunes, 22 de octubre de 2012
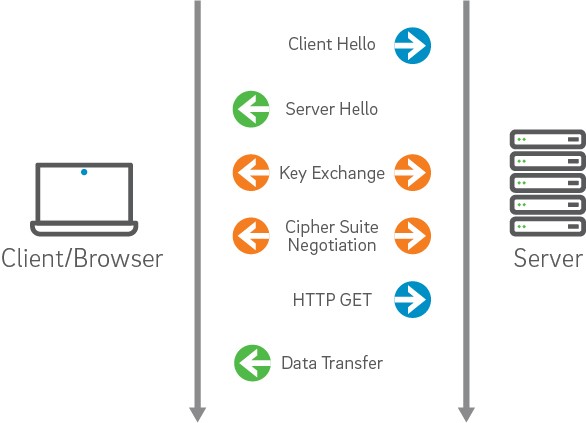
Practica generar SSL para IIS con Open SSL y Windows server 2003
En lo personal hacer esta practica fue una muy buena experiencia de aprendizaje ya que conocía un poco del tema pero no sabia lo que pasaba detrás del escenario delos certificados digitales para contenido web y en general no tube dificultades para realizarla el único fallo que tube es que en un principio me genero el certificado en otra ruta pero por que yo cerré la terminal y al volverla a abrir se coloco en la ruta por defecto lo único que volví a hacer es colocarme de nuevo en la carpeta bin del open ssl y listo tenia mis archivos para crear el certificado en la carpeta recomendada.
jueves, 27 de septiembre de 2012
Códigos de Cifrado Simétricos
Códigos de Cifrado Simétricos:
Explicare esto de una manera sencilla ya que entender como trabajan este tipo de códigos es muy fácil de entender.
Primeramente ¿que son los códigos de cifrado o encriptacion?:
Son aquellos que nos permiten esconder algo con un patrón para ocultarlos decir si lo que se quiere ocultar es algo escrito podemos hacer una sustitución de las letras por números para esconderlos. La encriptacion nos sirve para esconder información muy confidencial de posibles ataques, perdidas, robos, etc.
¿En que conciten los códigos de encriptacion simétricos?:
Haciendo referencia al ejemplo anterior los códigos simétricos consisten en que esas letras que se sustituyen por números siempre sean representadas por ese mismo numero para que el receptor del mensaje pueda descifrarlo aplicando esa misma metodología de manera inversa.
Ejemplo:
Vamos a hacer una representacion del ejemplo antes mencionado
A B C D E F G H I J K L M N Ñ O P Q R S T U V W X Y Z
.8 .5 .63 .11 .2 .31 .24 .6 .9 .7 .8 .4 .6 .61 .1 .0 .71 .35 .22 .54 .32.33 .35 .14 .71 .96 .66
de tal manera que si escribimos:
Hola mundo
El mensaje encriptado quedaría de la siguiente manera:
.6.0.4.8 .6.33.61.11.0
De esta manera el receptor al recibir el mansaje lo podra descifrar sustituyendo cada numero por la letra que le corresponde y esto es en lo que consiste basicamente el cifrado simétrico.
domingo, 23 de septiembre de 2012
BACK TRACK 5 R3 & ARP AND DNS SPOOFING
------------------BACK TRACK 5 R3 GENERAL REVIEW------------------
 Hello there this is a new entry, and in this time we are talking about one powerfull toll, like a swiss army knife of ha***ng, because has a lot of ha***ng apps and extended posibilities his name BackTrack 5 r3, is not an app or a web page its a operative sysem based on linux, and some aplications that you can find and his short description are:
Hello there this is a new entry, and in this time we are talking about one powerfull toll, like a swiss army knife of ha***ng, because has a lot of ha***ng apps and extended posibilities his name BackTrack 5 r3, is not an app or a web page its a operative sysem based on linux, and some aplications that you can find and his short description are:
*information Gathering:
A perfect tool to networking analysis, WLAN Analysis, Bluetooth, DNS, host analysis, network scaners, network trafic to made a vulnerabilities in this area.
*Vulnerability Assessment:
To check the open ports to find vulnerabilities, to open packages, and you can check a vulnerabilitie data base, and find shells ,you can do this whit (Cisco tools, Net fuzers, Open source Assessment, VOIP fuzer, vulnerability scaner ).
*Explotation Tools:
like his name says this tools works to find some bugs in network devices to explot then, whit your own objetives and purpouses.
*Privilege Escalation:
With this tool you can make a password attack redirecting the network trafic to your own computer, with the purpouse to obtain privileges up, all this whit snifers like ettercap, wireshark, and spoofing apps
*Maintaining Access:
It is to maintain the access whit back doors to evade a detection when you can save some privileges in a network server or another host.
*Reverse Engineering:
This apps can help you to open an instalation package like .exe, msi, msp, jar, nds, n64, etc. and check his code to see how works to you own purpouse
*RFID Tools:
With this radio frecuency identification you can make an analisys for this personal chips.
*Stress Testing
To attack servers speciali with DoS purpouse.
*Forencics:
Specially to encrypt your HD or find lose files and make a network analisys and save a RAM log
*Reporting Tools:
To make a report of an analisys
*Services:
Works to run Daemons of some servers.
*Miscelaneous:
This option has some network apps (Clients, networ and web).
------------------ARP SPOOFING OR ARP POISON ROUTING------------------
*Concept:
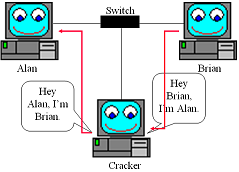
This type of attack can help you to be an intermediate in a network to see the trafic, change the trafic or stop the trafic DoS with some clicks, yhe packages to make the connection can be sended like a broadcast packages this type of packages can run in to the WLAN or LAN without previous identification and once inside the package can poison the traffic route.
*Personal point of view:
In my point of view this attack is amazing because you can see all the trafic of the network and you can use the collected data, to your own benefit the data that you can see are credentials, conversations, web request's, etc.
------------------DNS SPOOFING------------------
*Concept:

In this attak you can make a fake web server and you can redirect the trafic for this page to you server with the bjective to get the credentials of another person in the selected pages, in little words the victim go inside a page he type the DNS in his browser the request redirect to your own server and display the fake page the user type his credentials and when the victim type enter key the attaker get the credentials, the fake page display an error, and reload with the original page the user retype his credentials and get access at the page and he never think bad.
*Personal point of view:
In my opinion this is a specific attack the data that you need are the credentials and you can go for them with ARP Spoofing you can see the credentials too but its a general tool, with DNS Spoofing you make aspecific search.
------------------CONCLUSION------------------
In my personal conclusion i can say that both attaks are so good because they has a specific purpouse and both are very eficient, i cant say wich is better than the other because both are
diferent both are spoofing but you spoof diferent things, the focuse is diferent, i only can say that in my opinion the ARP Spoofing is a little wide because you can obtain the objective of DNS Spoofing and a plus of information like conversations and other things and this is fantastic, but the ARP Spoofing its more impactant because you can clone a web site and this is fantastic too, both attacks really like me and impact me so much.
ARP SPOOFING & DNS SPOOFING WHIT BACK TRACK 5R3
------------------BACK TRACK 5 R3 GENERAL REVIEW------------------
 Hello there this is a new entry, and in this time we are talking about one powerfull toll, like a swiss army knife of ha***ng, because has a lot of ha***ng apps and extended posibilities his name BackTrack 5 r3, and some aplications that you can find and his short description are:
Hello there this is a new entry, and in this time we are talking about one powerfull toll, like a swiss army knife of ha***ng, because has a lot of ha***ng apps and extended posibilities his name BackTrack 5 r3, and some aplications that you can find and his short description are:
*information Gathering:
A perfect tool to networking analysis, WLAN Analysis, Bluetooth, DNS, host analysis, network scaners, network trafic to made a vulnerabilities in this area.
*Vulnerability Assessment:
To check the open ports to find vulnerabilities, to open packages, and you can check a vulnerabilitie data base, and find shells ,you can do this whit (Cisco tools, Net fuzers, Open source Assessment, VOIP fuzer, vulnerability scaner ).
*Explotation Tools:
like his name says this tools works to find some bugs in network devices to explot then, whit your own objetives and purpouses.
*Privilege Escalation:
With this tool you can make a password attack redirecting the network trafic to your own computer, with the purpouse to obtain privileges up, all this whit snifers like ettercap, wireshark, and spoofing apps
*Maintaining Access:
It is to maintain the access whit back doors to evade a detection when you can save some privileges in a network server or another host.
*Reverse Engineering:
This apps can help you to open an instalation package like .exe, msi, msp, jar, nds, n64, etc. and check his code to see how works to you own purpouse
*RFID Tools:
With this radio frecuency identification you can make an analisys for this personal chips.
*Stress Testing
To attack servers speciali with DoS purpouse.
*Forencics:
Specially to encrypt your HD or find lose files and make a network analisys and save a RAM log
*Reporting Tools:
To make a report of an analisys
*Services:
Works to run Daemons of some servers.
*Miscelaneous:
This option has some network apps (Clients, networ and web).
------------------ARP SPOOFING OR ARP POISON ROUTING------------------
*Concept:
This type of attack can help you to be an intermediate in a network to see the trafic, change the trafic or stop the trafic DoS with some clicks, yhe packages to make the connection can be sended like a broadcast packages this type of packages can run in to the WLAN or LAN without previous identification and once inside the package can poison the traffic route.
*Personal point of view:
------------------DNS SPOOFING------------------
*Concept:
In this attak you can make a fake web server and you can redirect the trafic for this page to you server with the bjective to
*Personal point of view:
------------------CONCLUSION------------------
Suscribirse a:
Entradas (Atom)